In the “era reaching” transformation of information systems become the core foundation in all business activities. However, the relentless rise of the security threats, the network has put out urgent requirement on the construction of a security process closely comprehensive. According to research by IBM, average losses due to cyber attacks worldwide in the year 2023 has reached 4,35 million USD on every business – a number sufficient to clearly see the importance of protecting information systems.
This article Lac Viet Computing will help businesses understand the concept of “security processes, information systems“ get to know the benefits when implementing a strategy for effective security. This is a solid foundation to help business protect the assets of, maintain stability, to build trust with customers in the business environment is increasingly fierce.
1. Security processes, information systems, what is?
Security processes, information systems is the sequence of steps is designed to conduct a systematic way to protect the assets of your business from the threat to network security. This process includes not only the detect, prevent, but also ensure the ability to respond effectively, recover quickly after the incident, from which maintain the integrity, confidentiality and availability of information systems.
The core objectives:
- Protect integrity: Ensure data is not altered or removed illegal.
- Information security: Prevents unauthorized access to sensitive data.
- Availability: Ensure that the system always operates continuously, even when the incident occurs.
For example, A business application security process will build the protective layer from the network server, to the user, help minimize the risk of network attack in a comprehensive way.
2. Why business need security processes, information systems?
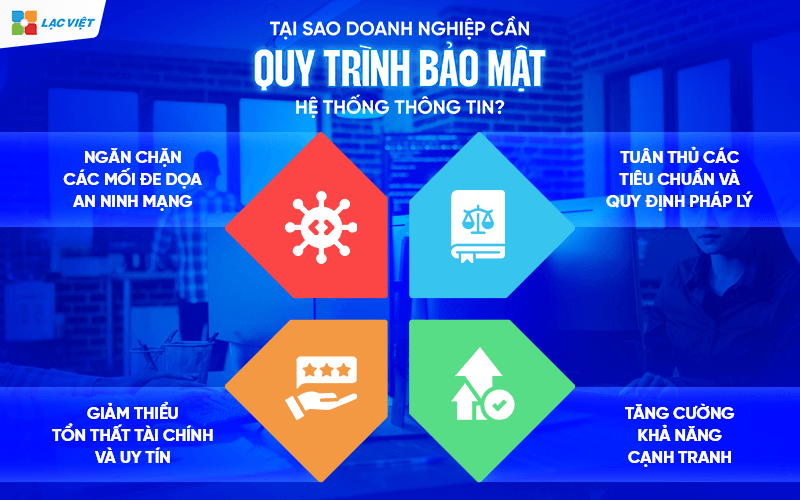
2.1 Stop the threat network security
Today, cyber attacks increasingly sophisticated, from ransomware, phishing to DDoS attacks. A security process, it helps businesses detect early signs of attack, deploy preventive measures effective.
The data demonstrate:
- According to IBM, 83% of businesses attacked network is because there is no process security full.
- The attack ransomware has increased 105% in the year 2023, causing serious losses on financial data business.
2.2 minimize financial losses and reputation
A cyber-attack not only cause data loss but also disrupt business operations negatively affect the brand reputation, customer confidence.
The attack ransomware targeted at a large hospital in the Uk in the year 2023 was disrupting the entire system in 2 weeks, causing losses of more than 5 million USD, undermines trust of patients in health services.
2.3 Compliance with the standards, legal regulations
The legal provisions on data security as GDPR (General Data Protection Regulation) in Europe or Decree 64/2017/ND-CP in Vietnam requires the organization to ensure information security for customer data. Non-compliance can lead to fines heavy influence to the brand.
A company in America was fined $ 80 million for failing to comply with privacy regulations that data of millions of customers leak.
2.4 strengthen competitiveness
A system safety information not only protect your business but also create competitive advantages to help businesses build trust with customers and partners.
For example, A technology company providing cloud service with process security standards ISO/IEC 27001 will attract more customers than rivals no security certificate.
3. The steps in security processes, information systems
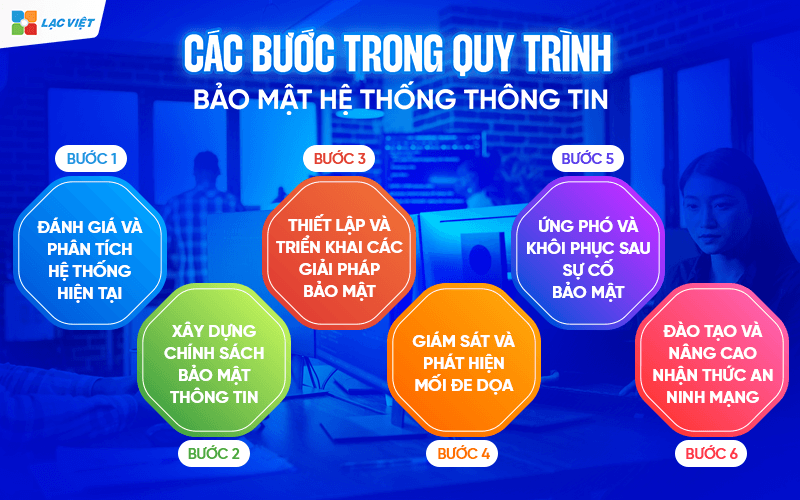
Step 1. Reviews analysis of the current system
This is the first step in security processes, information systems help businesses understand the current state of the system information, identify the flaw potential. The goal is to build comprehensive picture of the system, from which it proposed solutions appropriate security. The main activities:
Check the network configuration, server software:
- Analyze the current configuration of the system, network server to determine the set unsafe.
- Check the software application to ensure use of the latest update.
Log analysis and identify abnormal behavior: Data from the system log, firewall, application detection of unauthorized activity or unusual.
Use the scan tool vulnerability: tools such as Nessus, Qualys, or OpenVAS to scan the system automatically detects the security holes as wrong configuration, software error, or open service not required.
Results:
- Detailed report on the state of the system, the vulnerability is there, the level of priority fix.
- Reviews help businesses understand the potential risks, prepare the next step.
Step 2. Build privacy policy information
Privacy policy is document-oriented principles, security processes, information systems to ensure all employees and compliance standards for security throughout the enterprise. Content needed:
Rules use the password:
- Strong password requirements (minimum 12 characters, including numbers, uppercase letters, lowercase letters, special characters).
- Enable two-factor authentication (2FA) to increase the security.
Rules on data access:
- Apply the principle of Least Privilege (Only grant the minimum rights necessary for work).
- Authorization based on role, ensuring that only staff to be related to access of sensitive data.
Guide to troubleshooting:
- Specified the steps to be taken when detecting incidents, from the report to the process response.
- Ensure planning, data backup, system restore.
Benefits:
- Ensuring all employees perform the behavior, security, consistency, reduce risk from error human.
- Building a culture of security in the enterprise, enhance the sense of responsibility of each individual.
Step 3. Set the deployment of security solutions
Technological solutions needed:
- Firewall (Firewall): Is the first line of defense, helping prevent the unauthorized access to the system network of the business. Using Next-Generation Firewall (NGFW) to detect the threat as advanced as DDoS attacks, malware.
- Antivirus and Endpoint Security: protection of terminal equipment (computers, phones, servers) from malware. The common solution: Bitdefender, Symantec, Kaspersky Endpoint Security.
- Data Loss Prevention (DLP): Helps to prevent leakage or loss of sensitive data, especially customer data or internal documents important. DLP provides the ability to monitor, control, data moves through the system.
- Encryption (): data protection in a state of storage and transmission to ensure data can not be read if unauthorized access. Encryption should be applied to all files sensitivity, email, data storage on cloud.
Expected results:
- A security system, multi layer helps to comprehensive protection from network servers to the end user.
- Enhance the ability to detect, prevent threats before they cause harm.
Step 4.Monitoring threat detection
To detect and prevent threats to network security, enterprises need to build a system of comprehensive monitoring, continuous operation to monitor, analyze data from the information system.
IDS/IPS (detection System/intrusion prevention)
IDS (Intrusion Detection System) network monitoring to detect unusual activity, while IPS (Intrusion Prevention System) not only detect but also automatically stop the suspicious behavior.
Benefits:
- Timely detection of attacks such as DDoS, SQL Injection.
- Stop the flow of toxic before they cause harm to the system.
Popular tools: Snort (open source), Suricata, or Palo Alto Networks with features integrated IDS/IPS.
SIEM (Security Information and Event Management):
SIEM is integrated systems help businesses collect, analyze, and manage logs from many different sources, from that early detection of threat in cyber security.
Benefits:
- Provide the overall picture of network activity.
- Support incident investigations by providing detailed reports, traceability.
Popular tools: Splunk, IBM QRadar, Elastic SIEM.
Step 5. Response and recovery after a security incident
Respond quickly efficiently in the event of security incidents is the determining factor to minimize the damage. Process response need to ensure the correct consistency. The main steps:
- Fault detection, isolation regions affected: after discovering the incident, the system or staff need to identify quickly the area being attacked and isolated to prevent spread.
- Determine the cause, remove threat: analysis of the root causes of incidents, for example: software vulnerabilities, weak password, or device is compromised. Implementation of measures such as disconnection or removal by malicious software.
- Notice to stakeholders: Send notifications to the team, internal partners, or customers affected, ensure transparency.
System restore
- Data recovery: Use the backup copy (backup) to restore lost data, or encrypted by ransomware.
- Updated patch: fix the vulnerability has been exploited. Update the software, configure the system to prevent this issue from happening again.
Step 6. Training and awareness cyber security
Employees are important factors in security processes, information systems, but also the chain vulnerable to exploit the most. The training periodically to help raise awareness, skills security for all employees in the organization.
The training content:
- Identify the attack popular: By detecting email phishing or malicious links.Recognize the signs of malware on your computer.
- Account security: a guide to creating strong passwords, how to manage secure passwords.Integrated two-factor authentication (2FA) in critical applications.
- The process of reporting the incident: Staff need to know how to report suspicious activities to handled promptly. Use internal tools to quick report security incidents.
Frequency of training
- Organize training sessions periodically at least 3-6 months to update the threat, trends in cyber security new.
- Apply the test simulation (phishing simulation) to evaluate improve the response capabilities of employees.
Process security information system not only is an essential part in the strategic operation of the business but also the “shield” comprehensive protection against the threat to network security is increasingly sophisticated. Each step in the process which plays an important role in mitigating risk, ensuring stable operation.
4. Vietnam – more Than 30 years providing security solutions efficient information for your business
With over 30 years of experience in the field of providing technology solutions for business, Lac Viet is proud to be the pioneer in Vietnam in the deployment of security solutions, comprehensive information. We not only bring the technology advanced security but also provides deployment process professional, ensure the system of business always safe from the threat to network security.
4.1. Security solutions information systems from of Lac Viet
Lac Viet provider of security solutions varied in accordance with the needs and scale of each business:
- Firewall (Firewall): Use the system next-generation firewall (Next-Generation Firewall) to prevent unauthorized access, detect the threat raise.
- Antivirus and Endpoint Security: Integrated anti-virus software from prestigious brands such as Microsoft, Bitdefender, Kaspersky Lab,... to protect endpoints from malware.
- Detection system intrusion prevention (IDS/IPS): Detect, prevent timely acts of intrusion or flow anomalies on the network.
4.2. Deployment process security professional
Lac build process to deploy security with the clear steps to help businesses optimize system security:
- Reviews current system: comprehensive analysis of the security status determine the vulnerability implicit in IT infrastructure.
- The proposed optimal solution: Provide the solutions that fit the scale and budget of the business, ensuring the feasibility, long lasting effect.
- Deploy integration: our Team of professionals rich experience of Vietnam will deploy security systems, ensuring smooth integration of infrastructure out there.
- 24/7 technical support: After deployment, the technical team is always ready to support, system maintenance, ensuring continuous operation stability.
4.3. The outstanding advantage of security solutions from Vietnam
- In-depth experience: With more than 30 years serving thousands of businesses, Lac Viet understand all the needs and challenges of information security.
- Advanced technology: cooperation with the security firm leading companies such as Microsoft, McAfee, Avast to bring the most modern solutions.
- Customer service professional: deployment process flexibility, in-depth consultation, technical support and comprehensive to ensure the satisfaction of our customers.
4.4 Commitment from Vietnam
Lac Viet committed to bringing the business:
- Solution of comprehensive security: Ensure the confidentiality, integrity and availability of information systems.
- Peace of mind development: the Business can focus on your core business without worrying about security risks to the network.
- Updates latest technology: Always apply the technology advanced security to deal with the threat of increasingly sophisticated.
With a mission to accompany business in the transition of Vietnam to constantly improve the quality of service brought optimum value to our customers. Please contact with Vietnam today to get advice security processes, information systems and deploy solutions comprehensive security system for your information!