In the context of transformation of the enterprise increasingly depends on technology and data to operate the development. However, this dependence also comes with the risk of a network attack, one of the top threats for information security of the organization. According to reports from Cybersecurity Ventures in the year 2023, every 11 seconds, a business globally become victims of cyber attacks that cause the serious losses on financial credibility.
Clear awareness of the form of network attack is the first step for enterprises to build a security system firmly. This article Lac Viet Computing will:
- Explain in detail the form of network attack most popular today, as DDoS, Phishing, Malware, Man-in-the-Middle, SQL Injection.
- Analyze how the operation of each type of attack, thus helping the business to get to know the signs of risk.
- Giving directions in applied security solutions effective way to minimize risk, protect the system.
Let's find out in order to ensure that your business doesn't become the next victim of cyber attacks.
1. Network attack, what is?
Network attack is the action illegal entry or intentionally cause harm to computer system, network or data of the organization and the individual. These actions can be done by the individual, organization or group of hackers aims to vandalism, theft or appropriation of information.
The form of network attack is not only limited to the unauthorized access, which also includes:
- Spread malicious software (Malware): system or encrypted data to ransom.
- Hijack: Attack to manipulate or use the system of the business for their own purposes.
- Cause interruption of operation: Use the form as DDoS to crash the system.
Network attack is considered one of the greatest threats for businesses, especially in the digital age, where data – system online platform is the operating core.
The increase in cyber attacks during the conversion of
- Increase in the number of attacks: data from Check Point Research shows cyber attacks worldwide increased by 38% in 2023 compared with the previous year. The form of attacks increasingly sophisticated, diverse, difficult to detect, from DDoS attack overloads the system to ransomware to encrypt data for ransom.
- Vulnerabilities increase from the number conversion: the deployment of new technology, such as Cloud Computing, IoT, or AI that do not have security measures in full has created many vulnerabilities for hackers to exploit. According to Gartner, 90% of the security breach comes from error, human or wrong configuration.
2. The goal of network attacks
Network attacks are often targeted to one or more target below:
Theft data
Hackers aim to access, steal sensitive information, such as:
- Customer data: personal information, account numbers, or passwords.
- Business secrets: financial Data, strategy development, or the important contract.
For example, the attack on Equifax in 2017 reveal the information of 147 million people, causing losses of billions of DOLLARS for the company.
Destructive system
The goal is to interrupt or completely destroy the system of the organization:
- Delete important data: hackers can penetrate delete the entire database.
- Put the system into a state cannot use: Cause loss of control for the process is important.
Gain control
Hackers often attack to seize control system, the use for personal purposes, such as:
- Attack other organizations: Using server occupied rights pedal strike.
- Create botnet: Use the resources of the attacked system to perform DDoS attacks greater.
Harness the benefits of financial or political
- Ransom: The attack ransomware typically encrypts the data requires a ransom to restore.
- Pressure politics: The government organization is often the target of cyber attacks to influence political decisions or discredit.
3. The form of network attack popular many businesses are experiencing
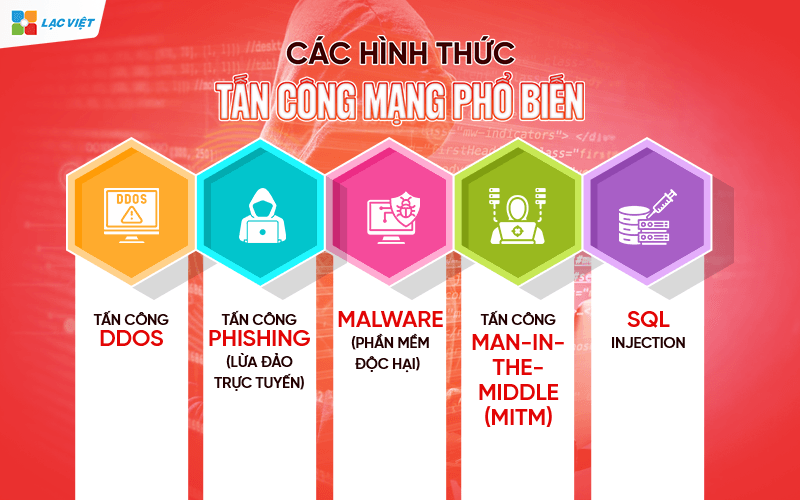
3.1. DDoS attack
DDoS attack is one in the form of network attack common to interrupt the operation of the system by sending a large request to the server, or network, that resource is overloaded, can't serve the request valid.
How it works:
- Hackers use botnets, consisting of thousands of devices have been compromised (PC, phone, IoT), to send traffic with large amount to the objective.
- When the system is overloaded, the online services become slow or stop working completely.
Practical example: DDoS attacks greatest 2023 aim at a finance company in Europe has created of fake traffic exceeded 71 million requests per second, interrupting business operations in 12 hours.
The solution prevention:
- System load balancer (Load Balancer): distributes traffic evenly between the server to reduce the load pressure.
- Security services DDoS dedicated: Use the solution such as Cloudflare or AWS Shield to identify, block traffic-toxic.
- Traffic monitoring: analyze network traffic to detect abnormal behaviors, preventing timely.
3.2. Attack Phishing (online fraud)
Phishing is a form of attack online fraud that aims to steal sensitive information of users, such as accounts, passwords, or financial information through email, message or website fake.
Identification signs:
- Email or message contains links to website tampered with interface similar official website.
- Email content often have language emergency as “your account is about to be locked” or “Updates the information immediately.”
- Attachments contain malware or spyware.
Statistic: 91% of cyber attacks derived from the form of Phishing, making this the most common modes (according to the Verizon Data Breach Report, 2023).
The solution prevention:
- Staff training: Organization of training sessions for staff to recognize the email or phishing links.
- Security solutions email: Use tools such as Secure Email Gateway to filter, block dangerous email.
- Two-factor authentication (2FA): enhanced account security to prevent unauthorized access even if the password is stolen.
3.3. Malware (malicious software)
Malware is malicious software designed to damage or gain unauthorized access to computer systems. The common types include virus, trojan, spyware, ransomware.
The type of Malware downloads:
- Virus: infection destructive data or program.
- Ransomware: data encryption requires a ransom to decrypt it.
- Trojan: Hidden within legitimate software to take control.
- Spyware: track stolen user information.
Consequences: Cause data loss, system, or complete paralysis. According to Check Point Research, ransomware has increased by 59% in the year 2023.
The solution prevention:
- Installed software anti-Malware: Use solutions like Malwarebytes or Bitdefender to detect remove Malware.
- System updates regularly: Make sure the patch latest security is applied.
- Process the data backup: Make backup periodically to minimize the risk of data loss due to Ransomware.
3.4. Attack Man-in-the-Middle (MITM)
MITM is a form of network attack in which hackers blocked, control communication between the two sides without being detected. This allows them to read, modify, or steal data during transmission.
Hackers blocked the connection of the user when they access the network of public Wi-Fi is not secure, then the stolen login information or sensitive data.
Identification signs:
- When connecting to a Wi-Fi browser-warning “connection is not secure” or not padlock icon on the address bar. Public Wi-Fi requires a login through a strange portal that is not of the service provider reliable.
- Network speed slow down suddenly without apparent reason, because traffic can be blocked or redirected.
- When visit sensitive sites (bank, e-commerce), browsers display a warning “invalid Certificate” or “SSL is fake.”
- Receive notifications from the service account on the login from an IP address or strange position that you didn't make.
The solution prevention:
- Use protocol encryption: Only connect to the website using HTTPS, apply VPN to encrypt data before transmission.
- Avoid using public Wi-Fi: No, visit the service sensitive (bank, email, company) on the public network.
- Verify SSL certificate: to Ensure the security certificates SSL/TLS is installed, used properly.
3.5. SQL Injection
SQL Injection is a form of attack on the database of the business. Hackers exploit vulnerabilities in web application to insert SQL code-toxic, from that steal or delete data.
Identification signs:
- SQL error on the user interface: Website showing error as “SQL syntax error” or “database error” when entering abnormal data in the input field (form, search bar). The error as “Unclosed quotation mark” or “Invalid column name” appears.
- Query or unusual activity in the database: customer information is edited or data loss without apparent reason. Discovered queries strange in the log of the database, especially the query is not due to the system or performing employees.
- Website performance is unusually slow: Website becomes slow when processing the query, so hackers try to perform the malicious query complexity to data mining.
- User file data, invalid or otherwise related in the report or the user interface.
Consequences: stolen customer information or sensitive data. Spoil or destruction of the database is important.
The solution prevention:
- Test patch application vulnerabilities: perform periodic inspections to detect the vulnerabilities in the source code.
- Use security tools: Web Application Firewall (WAF) such as ModSecurity help prevent the SQL Injection attack.
- Sanitizing input data: Ensure that all data entered into the system are examined and clean filter.
Understand the form of network attack such as DDoS, Phishing, Malware, MITM, SQL Injection is essential to business building prevention measures effective. The application of security technology, modern, raise awareness of network security will help reduce risks and protect critical systems.
4. Consequences of the attack network for business
4.1. Financial losses
Network attacks can cause serious losses on finance for business. Not only includes the cost of restoring the system, but also the expenses incurred other as compensation for customers, loss of revenue during the time the system is interrupted.
Cost of data recovery, the system:
- Businesses need to pay to recover data encrypted or delete by the attack ransomware.
- Invest in the solution, additional security after the incident.
- The cost to hire cyber security experts to analyze prevent the vulnerability.
- For example, An attack ransomware in the year 2023 at a hospital in the Uk has led this organization lost more than $ 5 million to restore the system data.
Loss of revenue due to disruption:
- In time the system is interrupted, business operations, such as deals, sales, offers services stalled.
- For example: DDoS attack on a floor-commerce in Vietnam has made sales dropped 20% in a week high point.
Customer compensation and the expenses incurred:
- Businesses have to pay damages to customers if their data is leaked or lost.
- Research from IBM (2023) to see the average cost of a data breach is 4,35 million USD.
4.2. Loss of brand reputation
Business reputation is an intangible asset, but very important. A cyber-attack not only lost the trust from the customers but also can have a lasting impact on brand image.
Lose the confidence of customers:
- Customers tend to stop using the services or products your business when your personal information, they leak.
- For example, the attack on the system of Marriott International (2018) reveal the personal information of more than 500 million customers, which leads to wave boycott strong from the user.
Negative effects on social media:
- Incident cyber attacks often attract great attention from the media, increase the severity of the issue in the public eye.
- Business label, lack of safety or not reliable.
Long-term impact to brand:
- It took many years for businesses to restore the reputation after an incident in cyber security.
- New customers may be hesitant to cooperate with business't under attack.
4.3. Legal consequences
In addition to financial losses and reputation, the form of network attack may entail legal consequences serious. Violation of regulations on data security not only makes business under penalty which also leads to the prolonged litigation.
Violation of the rules data security:
- According to the GDPR (General Data Protection Regulation) in Europe, the business can be fined up to 20 million Euros or 4% of global turnover if no protection is personal data of the customer.
- In Vietnam, Decree 64/2017/ND-CP requires the organization to comply with strict regulations about information security, including the deployment of measures to protect customer data.
Legal costs:
- Businesses have to pay attorney fees, handling disputes the account of administrative penalties.
- For example, A large bank in the U.s. was fined $ 80 million for failing to comply with regulations, data security after the leak customer information.
Lost the right to participate in the market: some countries or partner can apply the ban or limit cooperation with business violations of network security.
Businesses need to invest in security measures, comprehensive, from technology to training and awareness for staff, to minimize risk and protect the system against the threat of increasingly sophisticated.
5. Security solutions for effective business
5.1. Training and awareness cyber security for employees
Employees are your first line of defense from threats to network security, but can also be the weakest link if not trained properly. A study from Verizon (2023) indicated that 85% of the leak data related to bug people, mainly due to not recognize the email is phishing or use weak password.
Benefits of training:
- Help employees recognize the form of attacks such as phishing, malware.
- Building a culture of security in the enterprise.
- Reduce the risk to the behavior as safe as clicking on malicious links.
Training content:
- How to recognize email, sms scam.
- User guide strong password manager, password safe.
- The process of reporting cyber security incidents.
How to implement:
- Organization of seminars or courses periodically.
- Use the training platform online as KnowBe4 or Infosec IQ to simulate the attack scenarios realistic.
5.2. Applied technology advanced security
Modern technology played a key role in the protection system of business before the threat of increasingly sophisticated. Here are some solutions you need:
- Firewall (firewall): Block the unauthorized access to the system network. Should use Next-Generation Firewall (NGFW) as Cisco Firepower or Palo Alto to detect the threat as advanced as DDoS attacks, Malware.
- Endpoint Security: protect your terminal (computer, phone) from malicious software, network attacks. The common solution: Symantec Endpoint Protection, Kaspersky Endpoint Security.
- DLP (Data Loss Prevention): Prevent leakage or loss of important data. Track control data flow in/out system. Apply in the corporate store sensitive data such as banking and health.
- Detection system prevent attacks (IDS/IPS): network traffic Monitoring to detect unusual activity, stop immediately.
5.3. Check reviews periodic security
No security system is perfect. Therefore, the check periodic reviews help businesses timely detection of vulnerabilities, improve defense capabilities.
- Penetration Testing (testing penetration): simulation of attacks to detect processing flaws before hackers exploit. Other popular tools: Metasploit, Burp Suite, Nessus.
- Audit network security: a comprehensive Review of policies, processes and security technologies. Ensure compliance with the international standards such as ISO/IEC 27001 or the local regulations such as GDPR.
- Report – improved: After each round of tests, set up a detailed report of the problem detected is to put on an improvement plan.
5.4. Choice of partner security credits
The partner provides security solutions for business not only offers technology that also supports the construction business strategy comprehensive protection.
Criteria for selecting partners:
- Reputation in the field of network security.
- Provide solutions that fit the needs, budget of the business.
- Technical support, ongoing advice.
The leading partner:
- Cisco Systems: provider of network solutions, advanced security, such as NGFW, IDS/IPS.
- Palo Alto Networks: Famous with the system next-generation firewall, cloud security.
- Trend Micro: Provides protection solutions email, endpoint and network.
Cooperation:
- Work with partners to customize security solutions according to specific business.
- Planning to upgrade the system periodically to ensure always cope with the new threat.
Investing in security solutions not only help businesses minimize financial losses and reputation, but also create a solid foundation for the long-term development. Let's start by raising awareness for staff, technology deployment, security, modern, check the system periodically, in cooperation with the partner security credits for the construction of “the shield” comprehensive protection for IT systems of the enterprise.
6. Lac Viet provide security solutions comprehensive network for business
With over 30 years of experience in providing solutions in information security, Lac Viet is proud to be the leading unit in Vietnam in the protection system business before the threat to network security.
Lac Viet solutions provide comprehensive security data backup for business includes firewall, anti-virus software, the technology against intrusion from the security firm reputation as Microsoft, Bitdefender, Kaspersky Lab... With the technical team of highly professional development and professional technical support 24/7, Vietnam committed to bringing our customers absolute peace of mind, help information systems, stable operation safety before every challenge.
Cyber attacks are becoming a big threat for every business in the era of digitization. Understand the form of network attack along these signs get to know is the first step to protect system and data of the business from risks serious. Hope post content useful for business.